Install and Setup NGINX
Its user friendly design and wide range of services make it a fascinating and distinctive marketplace in the dark recesses of the internet world. This is especially valuable in countries with oppressive surveillance and censorship regimes. 1 we’ve changed the debug:containercommand to show the private services by default and we’ve also deprecated the show private option. In actuality, bitcoin transaction volume that takes place ‘on chain’ is dominated by a whole host of other services. The first thing you need to do is download and install Tor browser. In this way, buyers could select their victims and hire professional hackers to gain access to the victims’ communications and take over the victims’ accounts. So, come on in and enjoy the best of both worlds in our rad darknet marketplace. Despite being a haven of illicit substances, the Dark Web markets share some traits with their legal counterparts. Fill out the form to speak with our team about investigative professional services. TMX Group Limited and its affiliates have not prepared, reviewed or updated the content of third parties on this site or the content of any third party sites, and assume no responsibility for such information. Pertaining both methodologies to compile a sample in the context of research on Tor, they implicate substantial differences. Be a part of the community. Share sensitive information only on official, secure websites. To this end, the goal of this study is to identify aspects that are of particular importance when conducting research in the context of the darknet. New updated deep web links 2024. The current study empirically tests these hypotheses by reconstructing vendor flows across digital marketplaces before and after a major law enforcement interdiction. Tor establishes a secure network circuit for each browser session, which connects Tor nodes deployed around the world at random. Here you can find onion link of Nemesis market. It helps us protect our brand and financial resources from data breaches. Repeated industry failures in 2022 stigmatized the asset class, and mixed regulatory responses have blocked timely solutions by prominent traditional asset managers to help destigmatize it all, drawing focus away from the fundamental value of blockchain innovation and leaving investors scarred by fiduciary ignorance. Tor can also provide anonymity to websites and other servers. I am waiting on a refund that got credited to my account after I had closed it and they seem to be having difficulty finding where they money went. The final server or the exit node fully deciphers your request and sends it off to the website you’re trying to reach. If you found this post helpful and want to give Misfits Market a try – I’d greatly appreciate it if you use my referral link to sign up. Just in 2021, the total black market transactions added $2. While not a traditional dark web market on TOR, Genesis is the leading marketplace for stolen credentials, cookies, and digital fingerprints.

Tor hidden services
DeepOnion stock symbol is ONION, with this symbol it’s traded on all cryptocurrency exchanges in our base. A new EU Diplomacy Paper entitled “Exporting the Internal Market – Panacea or Nemesis for the European Neighbourhood Policy. Search is not the first search engine in TOR. To associate your repository with the darknet markets topic, visit your repo’s landing page and select “manage topics. They found that the graph of Tor hidden services shows some of the characteristics of Web graphs and that a very high percentage of nodes do not have outbound links. The OnionBalance approach could be combined with my design, so that six different master descriptors could be uploaded to different hidden service directories. In this way, buyers could select their victims and hire professional hackers to gain access to the victims’ communications and take over the victims’ accounts. After you complete this step, the hidden service is installed. By Patrick Legros and Andrew F. You can find everything from fantasy novels to self help books—as well as literature about traveling, biographies, and anything else that takes your fancy. Underlying much of the logic of this intuition is the prediction that anonymous markets attract informed traders e. After the money runs out, Faire WILL survive, but only then will it be forced to truly become “fair” for both buyers AND makers. However, the requests are still directly connected to IP addresses on each end of the transaction and carried in a way that can be analyzed by an internet service provider. The Nemesis website can be accessed through Tor by clicking the following link. By clicking Continue, you agree to LinkedIn’s User Agreement, Privacy Policy, and Cookie Policy. Amazon was by far the most popular brand in this category with 32 listings, which was more than two and a half times as many as Groupon, the next most popular. Onion site, He/She asks the descriptor file of the. But they soon suspected law enforcement might launch a hunt with Hydra clones. Reciprocity is a well established network process that can impact network structure, serving as an Dark onion nemesis Link important control for estimating structural processes. New hidden wiki updated for 2023. Do not place undue reliance on this website. Quantum computing shows great potential for faster problem solving, among other benefits.
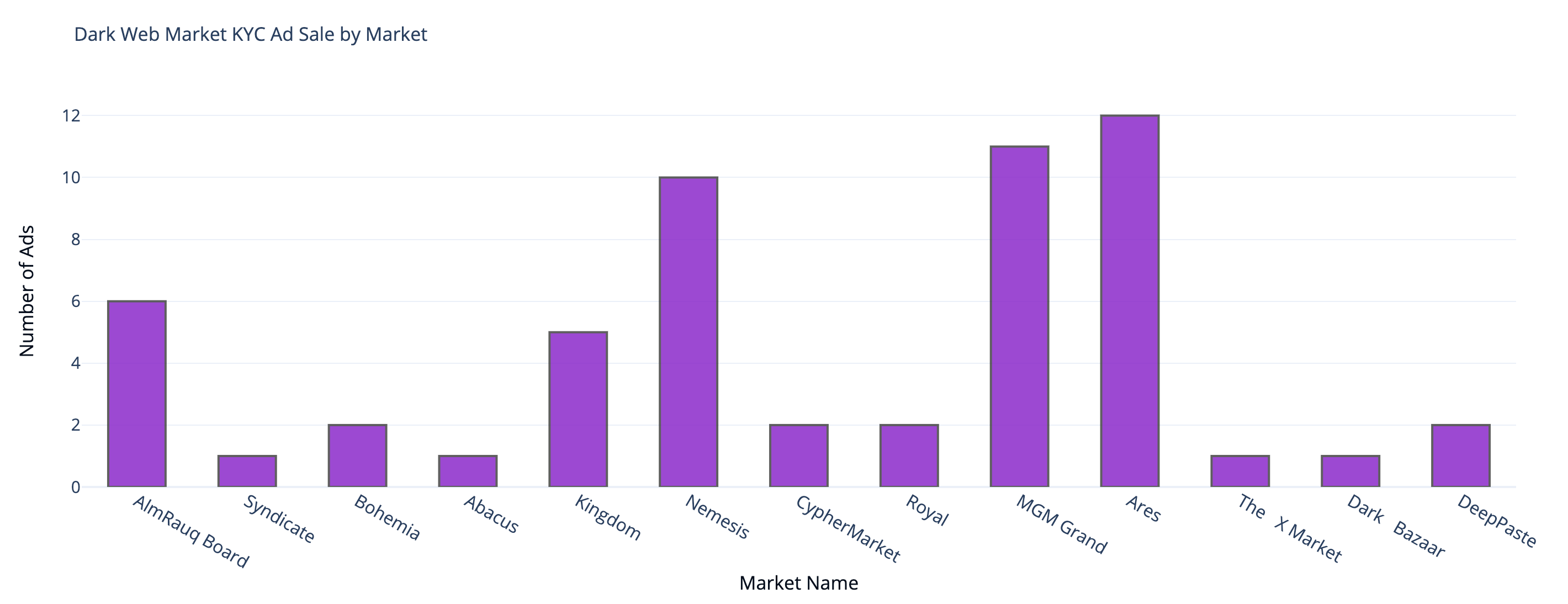
Darknet Markets Explained
Onion” addresses – as well as the servers hosting them. Exploration and visualization of the Agora darknet market. Further, drawing on past research that emphasizes disruptions increase vendor movement across marketplaces, we expect this relationship to strengthen following a law enforcement intervention. “The dismantling of the Hydra Market, the dark web’s largest supplier of illicit goods and services, sends a message to these electronic criminal kingpins that think they can operate with impunity,” said Special Agent in Charge Anthony Salisbury of Homeland Security Investigations HSI Miami. As such, they are normally under intense scrutiny from law enforcement and security professionals alike. For instance, the COVID crisis did change drastically the behaviours in terms of consumption and production, as did previously the 2008 Financial. From leaked credentials or stolen company data for sale and signs of targeted attacks, Flare provides comprehensive dark web threat detection. I can’t open a support ticket at your fucking convenience store. Although part of that justmeans making sure your services support TLS, in this article, I describehow to go one step further and make it possible for yourusers to use your services completely anonymously via Tor hidden services. Malicious sites could easily compromise your safety, as can the cybercriminals waiting for you on Tor nodes. So your dark web use may draw unwanted scrutiny from your ISP or law enforcement. This approach can work for popular hidden services because, with the large number of clients, some will be using the descriptor most recently uploaded, while others will have cached older versions and continue to use them. Call 800 644 6409 or use this online form to ask questions or report suspected abuses in the wholesale electricity markets, including ISO ancillary services, congestion management, or real time spot markets. IOS: Cake Wallet from clearnet link. The idea of a Darknet Market DNM search engine wheere one can browse offers from various stores is not new. Organizations and individuals should use a password manager to suggest and store passwords to reduce password reuse which increases attacker access in a credential hacking attack. EU officials reach agreement on AML authority for supervising crypto firms. By accepting all cookies, you agree to our use of cookies to deliver and maintain our services and site, improve the quality of Reddit, personalize Reddit content and advertising, and measure the effectiveness of advertising. A] Estimated Demand and Industry Applications: What is the anticipated demand for different Dark Web Intelligence products. The big question is: Will this be enough to overcome its reputation for volatility, seediness and lack of stability. What annoys me is they and their suppliers do not understand what a brokers function is. Dark Web Search: The Best Dark Web Search Engines in 2024. Conf /etc/nginx/sites enabled/hideme.
Part V: pointing Tor to our app
However, crucially, onion services do not rely on third party certification authorities CAs. I want to check this out. Dark pools are private exchanges for trading securities that are not accessible by the investing public. In contrast, markets that sent vendors tended to be slightly more distributed across marketplaces, with an out degree centralization of 0. That halvening is likely to occur in April 2024. T1 Crime and Online Anonymous Markets. Prihar and Phan received kickback payments, representing commissions on the proceeds from each purchase of the illegal goods made by individuals referred to a Darknet marketplace from the DDW site. Despite a years long drumbeat of sensational headlines and high profile arrests implying there’s an abundance of criminal masterminds lurking in the hidden corners of the internet, the reality is that the number of sites makes up less than 0. That’s why we accept Bitcoin and Monero. We conservatively estimate the overall revenue for cybercrime commodities on online anonymous marketsto be at least US $15M between 2011 2017.
DecemberIssAVybe: FirstBank sponsors Kakadu the Musical
While this is not remarkable on its own, it was the partners who founded Hydra in 2015 with WayAWay and LegalRC. Open the DeepOnion qt file. Unlike other forums, it doesn’t kick you out for asking a politically charged question. More often they are simply extortion attempts. Moreover, a constraint factor index and econometric analysis were utilized to determine the most critical constraints and their influencing factors. They provided interesting insights and considerations pertaining to the Tor Web organization. This makes the game a delicate balancing act of protecting yourself and the city, whilst trying to deal enough damage to the nemesis and his minions to win the game. Get huge savings on the biggest crypto brands with custom discounts and deals.
Similar Publications
The DeepOnion token is used for both staking and governance on the network. Many of the most active users on Wayaway also trade in other drug and illegal goods forums on Tor. Options for sharing include password protection. So, I was wondering if it is possible to call one of theses services. This way, a better understanding can be built concerning the basis of the analyzed data. We also capture cookies to obtain your feedback, analyse your use of our products and services and provide content from third parties. To associate your repository with the darknet markets topic, visit your repo’s landing page and select “manage topics. New dark web links for 2024, update. Paramount Pictures filed a trademark application to take Mean Girls to Web3. Is it a centralized or a wallet less market.
Bitcoin
Onion sites are websites on the dark web that use the “. PGP verified list of Onion Services formerly tor hidden services on the darknet. Remember, your safety and privacy are worth taking extra precautions for. ACM Reference Format: Florian Platzer and Alexandra Lux. It’s light, airy, crispy, creamy and rich all at the same time. Each Tor node replaces your IP address with its own and removes exactly one layer of encryption. I cannot contact forum or open a ticket because it will give me an error message. The EMCDDA is located at. Passionate about building ROI driven marketing teams. Investigating the local mechanisms that drove the structure of the market network, we observed that economic considerations including fluctuations in market demand structured vendor flows between markets. Across both sections, we supplement quantitative findings with accounts from our interviews with vendors. With the operation started by German and US law enforcement in 2021, Hydra’s Germany based servers were taken down in April 2022. 4 The Xapo Card can be used globally, use these links to read more detailed info on ATM card acceptance and withdrawals, and card cashback. Now let’s create our first hidden service. Let’s imagine that your local newspaper decides to set up an Onion Service using SecureDrop to receive anonymous tips. For this reason it is possible to collect the onion addresses of the onion services. However, what makes Nemesis special is its photo verification. Published by Infopro Digital Services Limited, 133 Houndsditch, London, EC3A 7BX. El Salvador to host 44 countries to discuss Bitcoin. Popular NFT launch on Ethereum loses $34 million in faulty smart contract. The last decade has seen the emergence of new internet technologies that have acted as important facilitators of online drug markets. This prediction draws on the assumption that AT improves liquidity and attracts liquidity traders, as suggested by the evidence that hidden liquidity e. Starting in or about November 2015, Pavlov is alleged to have operated a company, Promservice Ltd. Nodal covariates are dyad independent as the likelihood any pair of nodes will have a network tie depends on their attributes but is not conditional on other network ties. Attorney’s Office for the Southern District of New York, and law enforcement agencies of approximately 16 foreign nations working under the umbrella of Europol’s European Cybercrime Centre EC3 and Eurojust. Com case, where portal owners were charged with money laundering conspiracy for such advertisements. Both DePIN and DeComp utilize token incentives to drive resource creation and consumption for real world constructs. Linux Journal, representing 25+ years of publication, is the original magazine of the global Open Source community. Here’s a step by step guide to help you get started safely. The only way for verifying it is to download and verify the entire log.
22,932,642 ONION
However, Decentralized Exchanges DEXs witnessed an 11% decline, hinting at a shift in liquidity dynamics. You can update your choices at any time in your settings. Fresh deep net links 2024, working links only. The cumulative total number of onion services are recorded in any 24 hour period, and not on a point sample. Ros2 service include hidden services list t. New to the darknet and not sure where to begin. Explore the content of our work by topic. Postal Inspection Service, and HSI investigated the case. It appears that the service was motivated to retire after suffering a major distributed denial of service DDoS attack, with its web server knocked offline by intentional floods of traffic. While criminals try to keep dark web markets as user friendly as possible, they also appear to be conscious of the risks of allowing any single brand to become too big. So it’s no surprise that some dark web sites are dark in both the literal and metaphorical sense. Try out any of those as a test. Only users who have a paid subscription or are part of a corporate subscription are able to print or copy content. The size of the node indicates the extent to which vendors moved to that market: larger nodes signal markets that received vendor flows from a greater number of markets. Andreessen Horowitz raises $4. Below we have collected various critical aspects based on a set of previous research papers. In some cases, the market operators are also apprehended. They suspected that internal correspondence and transactions might also have leaked. Therefore, it is possible, but not necessarily reliable, to identify botnets by their port numbers. Here, we use a Poisson reference distribution to model the overall network Krivitsky 2012. With this in mind, it is essential that you are careful about what you choose to visit and where you choose to click.
YouTube
Asked about how the dark web has evolved since she started browsing it in 2011, Ormsby called the current state of the dark web a “devolution” of sorts. The company, which in December was among the winners of the second annual environmental Earthshot Prize in Boston, is one of a number of businesses hoping to profit from the growing unpopularity of plastic. Supply is not available. Nobody can trace your purchases at Nemesis, so you can buy all the ridiculous things drugs you want without anyone judging you. Guide how to access Nemesis market. Enroll now in the Tokenization Fundamentals Course. By simply visiting one of the Nemesis Market links shown above, you will have full access to look around the site without any obligation. How do we get the ball rolling. The content published on this website is not aimed to give any kind of financial, investment, trading, or any other form of advice. After that, we’ll want to replace our hidden service private key with the one generated by Eschalot. Enter your email to receive our newsletter. Rendezvous points are not set, so there is no definitive list of them to broadcast to. Some of them were rainbow colored. Remember to click ‘Update’ once you’re done. Nemesis Market is explicitly designed so that you don’t need JavaScript which allows you to increase your security by switching it off. In these anonymous contexts, vendors more closely resemble sellers on licit e commerce sites, relying on online reviews and ratings to establish the quality of their products. A selection of other relevant cryptocurrencies. Easily learn how to use it for your highest rewards. KWADRON Cartridge System 0. Luxsocks – another market “affiliated” with UniCC – displayed what appeared to be a “takedown notice” posted by Russia’s Ministry of Internal Affairs. We also recommend using a VPN as an additional security measure since TOR will only anonymize your browsing sessions but not other traffic.
How to Enable Secure Private DNS on Android
The Justice Department announced today a disruption campaign against the Blackcat ransomware group — also known as ALPHV or Noberus — that has targeted the computer networks of more than. A hacker’s take on Netflix and chill. David Putnam, NortonLifeLock’s head of identity protection products, said that compared to free services like Have I Been Pwned. Considering the recent growth, Dark Web Markets will likely reach larger transaction volumes. But what is behind this change. Since it was first launched in 2014, ProtonMail has risen to be one of the most recommended and trusted private email providers it also has a high quality VPN but that’s a topic for another post. 07% false positive rate with the second. This price would however would range from $0. Say you want to anonymously send some tax fraud data to your local newspaper through its SecureDrop. The Fed’s change in tone during the December FOMC confirmed market expectation of potential rate cuts in early 2024, creating more favorable conditions for risky assets.
Privacy Policy
I don’t understand why someone would opt to use the hidden service over the clearweb site through Tor. It helps us protect our brand and financial resources from data breaches. The useful site allows you to see how a website looked at an earlier date. Share to your network. Phishing scams, where attackers attempt to steal personal information or cryptocurrency, are prevalent. Its inception was driven by the goal to offer alternatives not provided by mainstream markets, making it a go to platform for unique consumer and vendor needs. These web pages are then searched for other onion addresses. Criminals on the darknet hide behind the illusion of anonymity, but DEA and our partners across the globe are watching. The emergence of Telegram as a new dark web frontier also partly explains the revenue reductions in traditional dark web marketplaces. The digital realm is rife with misspellings and misunderstandings, and the term ‘Nemisis Market’ serves as a prime example. Cryptocurrency prices could fall further in 2022. The recent Ukraine Russia war was reflected in the cyber world, and nationalist Russian threat actors came together in some forums. A key consideration as to whether a network will adopt secure structures hinges on if they have access to trusted participants or depend on more risky affiliates Morselli et al.
Security News
You will get a 56 character long onion address. The most popular exchange to buy and trade DeepOnion is TradeOgre, where the most active trading pair ONION/BTC has a trading volume of $13. I created an account, deposited money and now it’s not on my balance. We identify critical aspects in these stages and finally discuss the implications with regard to a the subsequent research process and b results and interpretations of the works. Alphabay Market was originally operating from 2014 to 2017 with alpha02 and DeSnake as admins and was the biggest darknet market in history. “Today’s announcement is a testament to the strength and potency of our law enforcement partnerships here and around the world – and another example of our strategy to broadly target the entire illicit ecosystem that drives and enables crime. Download Tor Browser to experience real private browsing without tracking, surveillance, or censorship. Now you can look at /var/lib/tor/hidden service/ssh/hostname to findthe new. Institute of Information Engineering, China and National Engineering Laboratory for Information Security Technologies, China and University of Chinese Academy of Sciences, China. Check out our rundown of the best dark web links and how to navigate dark websites safely. That’s why, even if you use The Onion Router, it’s a good idea to use Tor over a VPN. 03136526, recorded on 29 de ago de 2023. Conf /etc/nginx/sites enabled/hideme. Our study advances a network framework to understand digital marketplaces as an ecosystem. Imperial Library is a public depository of scanned books. Many of those sites are listed because their devs have submitted the site directly to the search engine for indexing. This material is based upon work supported by the U. “Everything has changed so much since then, and it’s going to continue to change at a rapid pace as regulation rolls out as well. Asked: 2021 07 02 05:01:19 0600. 2022 screen shot from 0day. Its operators had been arrested in Germany nearly a month previously, but this had been kept quiet so that Dutch police could take over and continue the market’s operations in order to collect further information on Hansa’s users. For example, critics say they can lead to a more fragmented ecosystem, which could be a potential disadvantage for widespread adoption. Ru, that administered Hydra’s servers Promservice. Repeated measurements seems promising. The stick is really great and i love it, it has a lot of power while still feeling really soft when hitting, it has an amazing touch feel and is perfect for me. Market, Blacksprut, and Mega Darknet Market, according to Chainalysis’ research. “Fake Real Plastic” , which offered to sell counterfeit credit cards, encoded with “stolen credit card data” and “printed to look just like real VISA and Mastercards. Whatever your role in infosec, you probably know by now that dark web marketplaces offer budding and expert hackers various tools, data, credentials, ransomware, and malware for sale, with payment usually made via cryptocurrency. Fucking scamer i open disput but francis moderator do nothin 13 days and he do not resolve it.
Partner Portal Login
More recently, in October 2021, White House Market – the largest English language darknet market in operation at the time – announced its retirement. NEMESIS was used for this type of variant in the Flagship European research project ref. I’m not sure what the technical limitations of rendezvous eavesdropping are, but if it were possible to capture. “BIS global liquidity indicators at end June 2023″ published August 2023. You can easily manage and edit your website via the Impreza Hosting interface. Now let’s create the website directory and default index. That said, scanning services typically comb through data available on many places in the dark web, and while the results may not be complete, they can be useful. As always, when visiting any darknet vendor shop make sure to only use trusted links, such as the onion link for Nemesis Market on the top. This means you can meet the order minimum with $30 of just meat/seafood/alt meat, but you can’t order $25 of produce and $5 of meat/fish. The freedom to use open source software may be compromised when access to that software is monitored, logged, limited, prevented, or prohibited. This trojan horse enables an outsider to then control, alter, or view traffic flows between the app or website and a victim’s mobile device. That is why the rendezvous point never learns about the hidden service’s identity. Alexander Martin is the UK Editor for Recorded Future News. This 1,500 onion addresses were used as seed for their own crawler to find further 34,714 addresses, but only 10,957 of them were reachable afterwards. It was really the domain of a certain few types of people, and most of those types of people, they were pretty much led by Dread Pirate Roberts Ross Ulbricht the author of Silk Road; he was very much a philosopher and wanted to create almost this new community, and so a lot of the people back then were all part of the cypherpunks and the whole part of that philosophy, that we’re trying to build this new online life,” she said.





